Admiral Nelson, Identity, and the Internet of Things
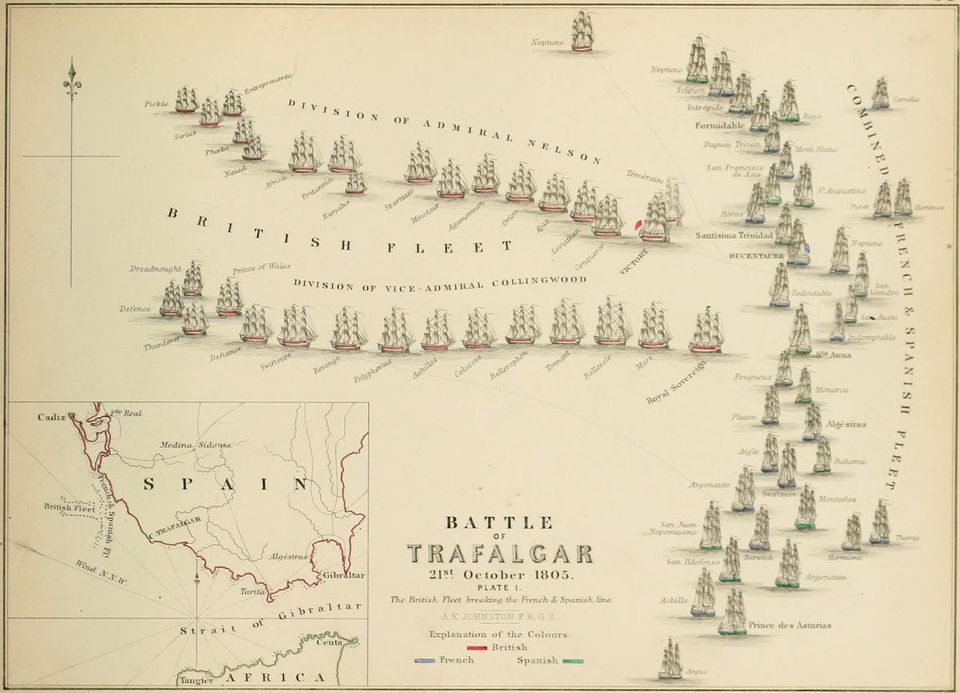
On October 21, 1805, the world changed. At the Battle of Trafalgar, British Admiral Horatio Nelson introduced a new strategy for naval warfare. Instead of lining up in a firing line opposite the enemy, he sailed his fleet directly into the enemy lines. The resulting chaos meant that sailors could no longer rely on location to identify friend and foe. Instead, Nelson redefined his understanding of identity: legend states that he painted his ships in a unique pattern so that the identity of each ship was obvious. This enabled his entire fleet—every ship, every sailor—to act instantly and independently in the pursuit of victory. Knowing this, he sailed into battle with a single order of battle: “It is expected that every person will do their duty.” The British Navy won a decisive victory, and naval warfare would never be the same.
Today’s organizations find themselves at a similar inflection point; the rise of the Internet of Things is changing the business landscape. One estimate cites that over 50 billion devices will be internet connected in the next three years, and businesses are seeking to harness this new capability: Gartner estimates that over 73% of organizations will have an IoT initiative by next year. These initiatives will usher in a wave of devices, agents, and programs that are enticing targets for malicious actors. More significantly, 85% of those IoT initiatives expect that their identity program will support them. The Internet of Things is coming, and identity programs are expected to govern them. How can we, like Nelson, wield the power of identity? How can we seamlessly adopt them into an existing identity governance program and identity-enable them to be simultaneously productive and secure? How can we issue a single order of battle, “It is expected that every identity-enabled entity will do their duty?”
Our understanding of identity must expand to incorporate this new set of entities ushered in by the Internet of Things. First, we must examine the full range of devices, agents, and programs in order to discern where they fall within the IoT spectrum and their potential threat level. The associated threat level may then be determined, along with the level of required governance. By applying well-understood existing identity models (e.g. contractor or employee), with slight modifications where appropriate, we can extend identity governance to this new class of actors, transforming the Internet of Things into the Identity of Things.
The Internet of Things Spectrum and Existing Identity Models
The Internet of Things is a diverse set of devices, agents, and programs—it is helpful to think of this collection as a continuous spectrum. On the low end of the spectrum are passive devices that are connected to the network but have little autonomy. A good example of this end of the spectrum is a security camera that provides surveillance. Passive devices do not merit an identity; they instead require access protection and a regular cycling of credentials that allow device access, something akin to Privileged Account Management.
Moving up the spectrum introduces independent agents. These are often programs or “bots” that take on specific tasks for the organization. Robotic Process Automation (RPA) falls squarely into this zone. Agents have some access to resources and can effect change, but these activities are limited. A customer service bot that responds to questions about order status might be a relevant example of this middle section of the spectrum. This increased access and the ability to initiate action means that governance is required and thus an identity must be assigned. However, since this access and control is limited, “bots” may be treated as contractors, with their access and control time-limited and constrained.
At the upper end of the spectrum, sophisticated artificial intelligence-based programs await. Limits on access are minimal, and these programs have the ability invoke actions as necessary. The unlimited potential of AI captures the imagination, as does its dangers (as an entire genre of movies has illustrated). Clearly, these higher order actors require full governance, and therefore should be treated like full employees of the organization.
All entities within the Internet of Things fall somewhere on this spectrum. Movement upwards along the continuum—from passive agents to independent agents to artificial intelligence—results in an increase in access to resources and the ability to initiate change in the environment. Consequently, it signals an associated increase in risk to the organization. It also increases the likelihood that an identity should be assigned—an identity that must be governed according to well-understood models in order to mitigate that elevated risk.
The Power of Identity and the Internet of Things
The Internet of Things is changing how businesses operate, and governing these new devices, bots, and AI requires a reevaluation of identity. Just as in Nelson’s day, an evolution in strategy—one that seeks to identity-enable the Internet of Things—is essential to success. Such a strategy demonstrates the power of identity to enable businesses to embrace this new technology and to capitalize on the change that accompanies it.
Organizations deploying this strategy can then, like Nelson, issue a single order of battle: “It is expected that every identity-enabled entity will do their duty.”